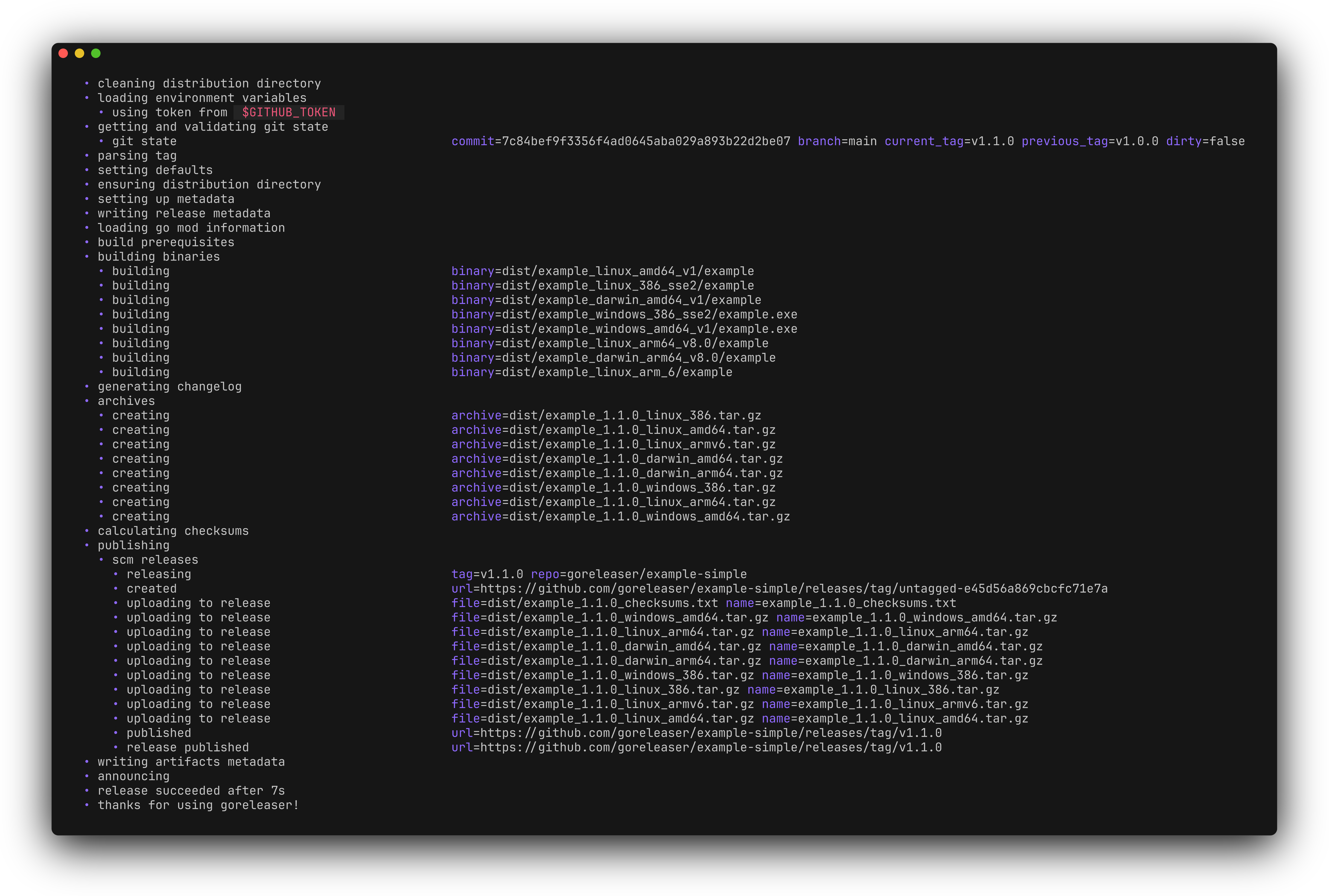
Release engineering, simplified.
We handle the complexities of releasing so you can focus in building what really matters: your software - and it doesn't need to be written in Go!
Get started Pro
Everything you need to release with confidence
GoReleaser does everything you need to create a professional release process for Go, Rust, TypeScript, Zig, and Python projects.
Fast & Automated
From commit to a release in seconds - automate your entire workflow with a single command.
Multiple Languages
First-class support for Go, Rust, TypeScript, Python, and Zig projects.
Cross-Platform
Build and release for multiple platforms and architectures.
Multiple Formats
Package your software exactly how your users want it - from binaries to Docker images and system packages.
Package Managers
Automatically publish to Homebrew, Scoop, Winget, AUR, Nix, and more.
Security Made Easy
Release with confidence using built-in SBOM generation, code signing, and notarization.
GitHub Actions and beyond
Works seamlessly with GitHub Actions, GitLab CI, and other popular CI/CD platforms.
AI Ready
Easily integrate with AI tools using the GoReleaser MCP.
What's changed?
Keep users informed with auto-generated, customizable changelogs for every release.
Let your users know
Announce releases to 𝕏, Slack, Discord, and more.
Trusted by Industry Leaders
Join thousands of developers and companies who rely on GoReleaser for their mission-critical releases.
Microsoft
AWS
Shopify
Uber
Splunk
Datadog
Hashicorp
GitHub
Grafana
Kubernetes
NGinx
Supported by Amazing Sponsors
These are some of the companies that help make GoReleaser possible. Become a sponsor!